What is Honeypot in Cyber Security? Types, Benefits, and Implementation
Table of Content
Download Paymattic – it’s Free!

Subscribe To Get
WordPress Guides, Tips, and Tutorials
We will never spam you. We will only send you product updates and tips.
Have you ever thought of luring cyber attackers to your website? It may sound like a lunatic’s delusion to you. But trust me, it’s not. You can’t solve any problem unless you’re facing one. So, smart people are now attracting malware attacks to their sites to analyze the threats and loopholes.
That’s what the Honeypot security system does. It creates a mimic system or network that fascinates cybercriminals to choose the wrong pathway rather than the real one.
By setting up these decoys, you can gain valuable insights into their tactics, techniques, and procedures (TTPs).
So this article is written only to let you know how honeypots work and their types, and to discuss the benefits and best practices for implementing honeypots in cybersecurity strategies.
What is honeypot security?
Honeypot security is a clever cybersecurity strategy that acts like a digital decoy, designed to lure cybercriminals into a trap and keep them away from legitimate targets. Imagine a baited honey jar in the middle of a forest; it looks tempting, but actually, it’s there to attract and capture intruders.
In the digital landscape, Honeypot security mimics a vulnerable system or network that draws hackers who think they’ve found an easy target. Once they’re inside the honeypot trap, they’ll be in a controlled environment, away from the actual target, revealing their tactics and methods.
Cyber experts will monitor, detect, and learn from malicious activities without compromising the actual assets. This will give them a complete idea of how the attackers access the site and explicit data.
This enables cyber professionals to detect threats, collect crucial data, identify potential blind spots, and develop more effective security policies to counter their strategies.
How do Honeypots work?
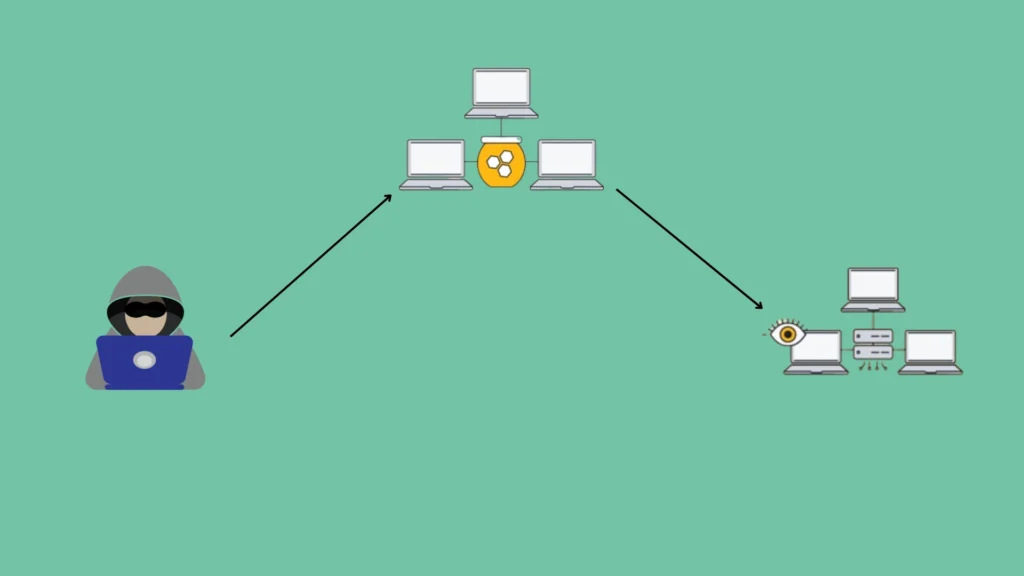
As described, honeypots are strategic tools in cybersecurity that are designed to attract potential attackers by mimicking real systems and networks. It could make a copy of the real computer system with fake data and applications that fool the attackers into thinking it’s the real target.
For example, it could mimic payment forms, billing systems, or payment gateways that are highly attractive to cybercriminals as they contain highly confidential information.
It can be used in bank IT security. You might set up a honeypot security system for outsiders or hackers as similar to the bank server. It’ll help you to protect the real server by diverting malicious traffic to the fake one.
Once they break into the honeypot, they’ll be in a completely controlled network. You can track them, their movement, and better understand their motivations.
Honeypots use a security vulnerability that is not subtle enough to be immediately noticeable yet obvious enough that most cybercriminals wouldn’t resist the opportunity to exploit it and gain access to the system.
A honeypot might have ports that respond to a port scan or use weak passwords. These vulnerable ports could be intentionally left open to lure attackers into the honeypot environment, diverting them away from the more secure live network.
By analyzing their movement and techniques, you can strengthen your security system to keep the real asset safe.
Moreover, there are many types of honeypots in cybersecurity that work differently.
Types of honeypot security
There are two primary types of honeypots available based on the design and deployment.
Production Honeypots
Production Honeypots are deployed within an organization’s live environment, typically alongside real servers and services. Their primary function is to act as decoys to lure attackers away from critical systems. These honeypots mimic genuine assets, such as databases or web servers, but contain no sensitive information.
Research Honeypots
Research Honeypots are used primarily by cybersecurity researchers to study the behavior, techniques, and tools used by cybercriminals. Unlike production honeypots, these are not meant to protect specific assets but to collect data on various attack vectors.
Research Honeypots are often set up to be highly interactive, allowing attackers to fully engage with the system. The collected data is then analyzed to identify new threats, understand the motives behind attacks, and develop more effective security strategies.
Depending on the level of complexity, Honeypot security is classified into four categories.
Pure Honeypot
Pure Honeypots are full-fledged, highly interactive honeypots that simulate entire networks. These complex setups closely resemble a real network environment, including multiple systems, services, and users.
Pure Honeypots are designed to capture extensive information about an attack, including the attacker’s tools, techniques, and progression through the network. This type of honeypot is often used in research to gather in-depth insights into sophisticated attack patterns.
Low-Interaction Honeypots
Low-interaction honeypots simulate specific services or ports on a network but do not offer a full operating system for attackers to interact with. They are easier to deploy and manage compared to high-interaction honeypots.
Low-interaction honeypots are designed to capture basic information about automated attacks or common exploits, such as login attempts or port scans. While they provide less data than high-interaction honeypots, they are valuable for quickly identifying common threats and malicious activity.
Mid-interaction Honeypots
Mid-interaction Honeypots mimic components of the application layer without including an actual operating system. Their purpose is to mislead or confuse the attackers, giving the organization extra time to analyze the nature of the attack and prepare an appropriate response.
High-Interaction Honeypots
High-interaction honeypots offer a more realistic environment, allowing attackers to interact with a full operating system and perform a wide range of activities. The main target is to encourage attackers to spend as much time as possible within the trap.
So the security team gets more opportunities to monitor the attacker’s objectives and strategies, as well as to identify potential vulnerabilities within the system.
High-interaction honeypots simulate a more complete and realistic environment, so they require more resources and careful management to avoid becoming a liability if compromised.
For different types of threats and cybercriminals, there are some other types of honeypots available to react to.
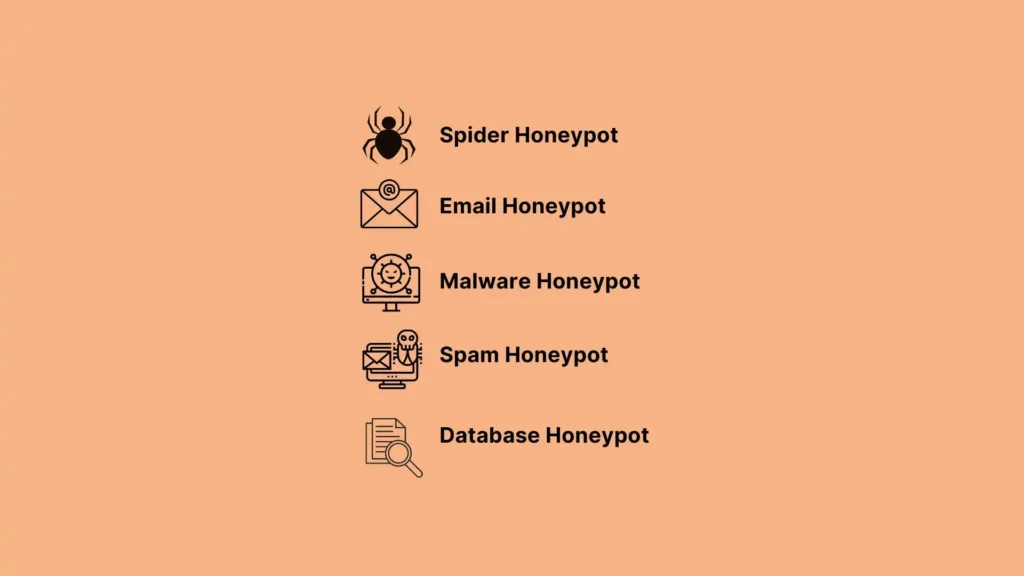
Email Honeypot
Email Honeypots are also known as email traps or spam traps. It’s a specialized type of honeypot security designed to attract and trap email-based threats, such as spam or phishing attempts.
It involves creating fake email addresses or mail servers in a hidden field that can only be detected by automated bots and is not visible for any legitimate communication. As long as it started receiving emails, you can categorize them as spam and block the sender and IP address as well.
Malware Honeypot
A Malware Honeypot is a decoy system that replicates software applications and APIs to lure in malware attacks. By analyzing the attacks, you can identify the API weaknesses and develop anti-malware software.
Spider Honeypot
A Spider Honeypot is specifically designed to attract and trap web crawlers, or “spiders,” by creating web pages or links that are only accessible to crawlers or bots. By detecting spiders, you can improve security measures and protect legitimate web traffic.
Subscribe Newsletter
Subscribe to our newsletter for updates, exclusive offers, and news you won’t miss!

Benefits of using Honeypot in cybersecurity
Having a strong security system is the first task for any organization. To do this, businesses use different types of anti-spam plugins for WordPress. These plugins will work to prevent cyberattacks.
But honeypot functions differently there. It attracts malicious attacks to find the loopholes and develop them. Their primary goal is to expose vulnerabilities in existing systems and redirect hackers away from genuine targets.
Using a honeypot in cybersecurity offers several advantages.
- Threat Detection: Honeypot helps identify new or emerging threats by luring attackers into a controlled environment where their techniques and tools can be observed.
- Behavioral Analysis: They allow for the analysis of attacker behavior and tactics, helping security professionals understand the attack methods and develop better defenses.
- Vulnerability Identification: By observing how attackers exploit honeypots, organizations can identify and patch vulnerabilities in their real systems.
- Research and Development: Honeypots can be used to gather data on malware and attack strategies, which can be valuable for developing new security technologies and strategies.
- Deception and Distraction: Honeypots divert attackers away from valuable systems and data, buying time for security teams to respond and strengthen defenses.
- Low maintenance: Honeypot only interacts with malicious activities. So once you implement them, they run by their own monitoring. You don’t need to keep your eyes on it every time.
Having said that, there are two sides to a coin. It has some drawbacks also. As such:
- Honeypots only detect attacks that target them directly. If an attacker bypasses the honeypot, it can’t track them.
- If a honeypot is compromised, it could be used to launch attacks on other systems.
- Skilled attackers may detect the honeypot and either avoid it or deliberately attack it in ways that provide misleading information.
- The data collected from honeypots can be complex and difficult to analyze, requiring specialized knowledge to extract meaningful insights.
How to use Honeypot in WordPress
There are many software available in WordPress that offer honeypot security tools. But Paymattic offers the simplest way to integrate honeypot security into your WordPress website completely free.
Believe me, you can’t even imagine how simple it is to integrate Honeypot in cybersecurity with this plugin.
- Go to your WordPress admin dashboard
- Click on Plugins → Add New
- Search for Paymattic and install the plugin
- Click on the Activate button
After activating Paymattic,
- Go to Settings → General Settings
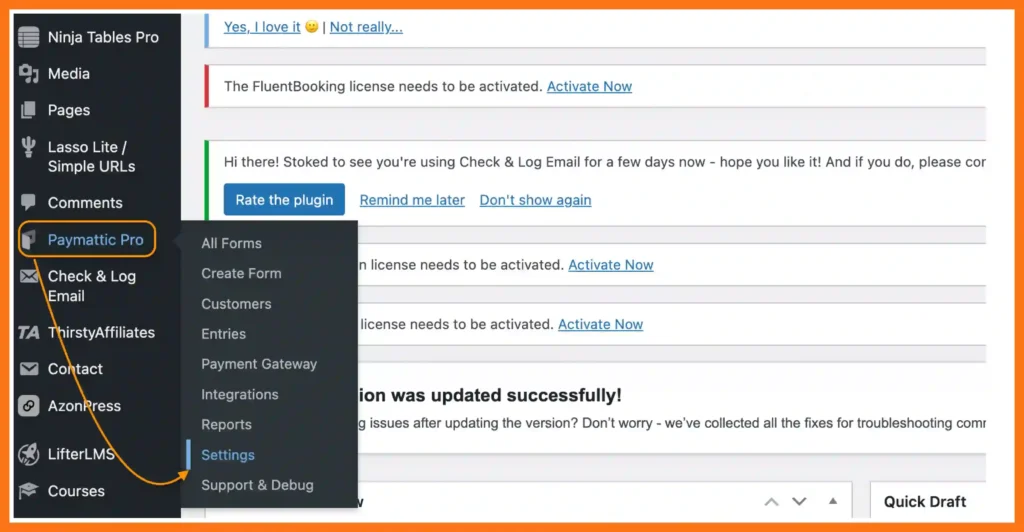
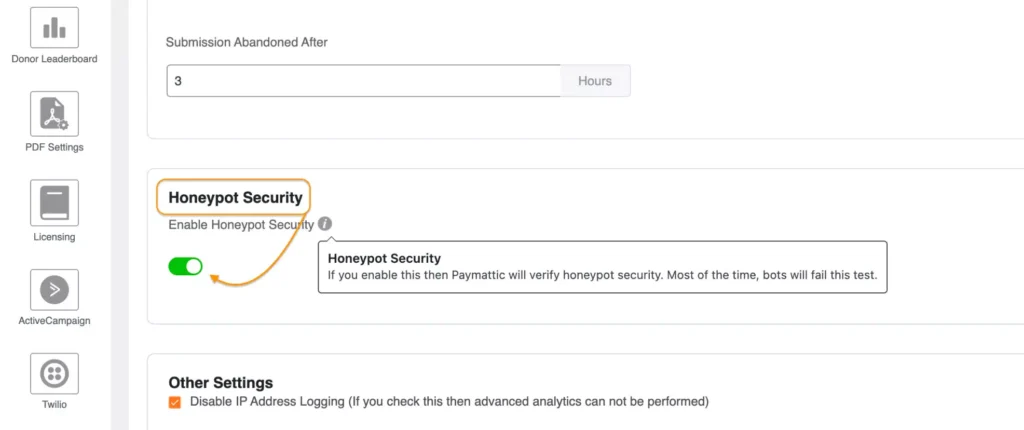
The funny thing is, once you click on Settings, it’ll automatically take you to the General Settings.
Scrolling down a bit, you’ll find an option to Enable Honeypot Security. Just toggle it, and you’re done. Yes, you heard it right; it’s that simple.
Wrapping up
By understanding the benefits and various types of Honeypot security systems, organizations can effectively deploy them to detect threats, study attacker behavior, and strengthen their overall security posture.
However, successful implementation requires careful planning, ongoing management, and a clear understanding of the potential risks involved. When used wisely, honeypot security can be a critical asset in the fight against cyber threats, that help safeguard real systems and data from malicious attacks.
Join the thousands already enjoying Paymattic Pro!










Leave a Reply